We've reached the final post in our Ansible Vault series. We've come a long way and have just scratched the surface on how Ansible Vault can be used to help secure automation.
You've learned to stop hardcoding passwords by encrypting entire files. You've mastered surgical security by encrypting s...
Over the past few weeks, we've explored Ansible Vault, learning about its purpose and how it can be utilized. You can create fully encrypted files and perform granular, inline encryption on single variables. Your secrets, hopefully, are no longer stored in plain text.
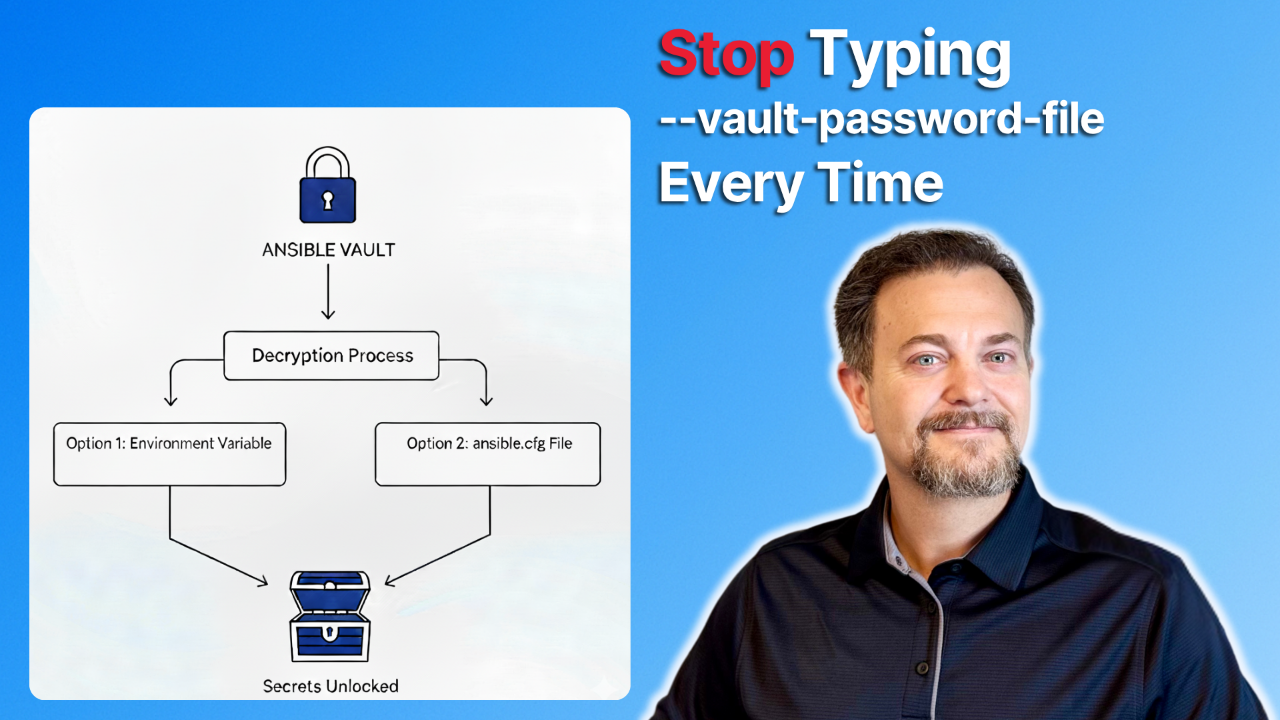
But there's still one manual...
In our last post, you learned how to create a fully encrypted file with ansible-vault create. This is the perfect solution for grouping a set of related secrets, like all the credentials for a new SQL Server build.
But what happens when you don't need to lock down an entire file?
Sometimes, you h...
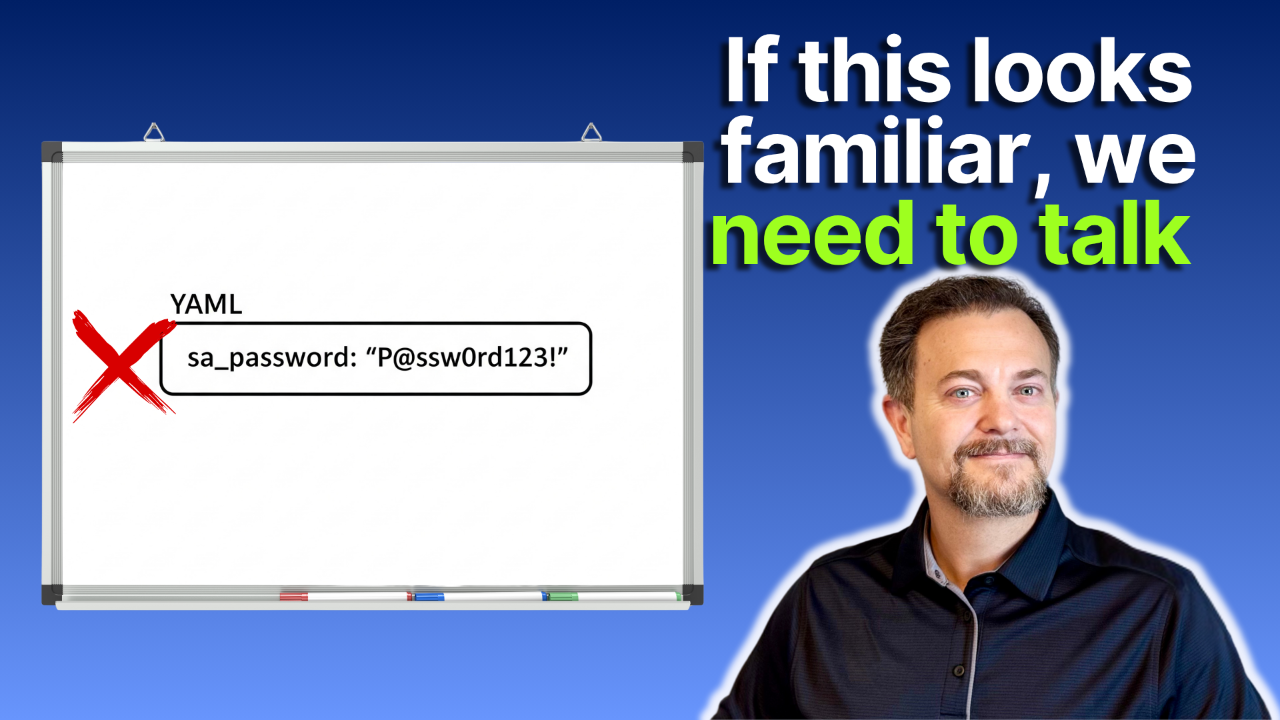
Let's be honest with each other. We've all done it.
Whether it was a late-night deployment script, a quick and dirty data load process, or a configuration change, we've all hardcoded a password in plain text. It feels fast. It gets the job done. And in that moment, it feels harmless.
But that ...
Edition: Saturday, June 29th, 2024
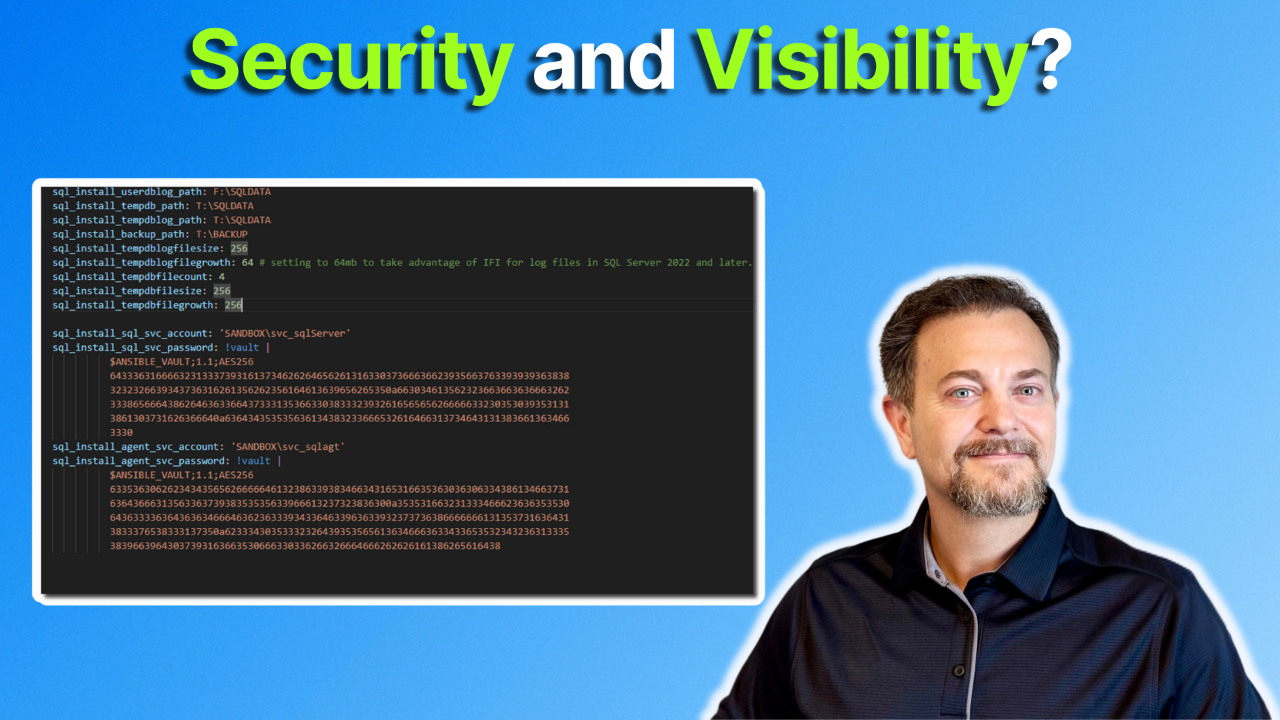
Storing passwords in plain text files is a big problem. Such as the SA password when working with SQL Server. But how do you automate the installation of SQL Server and store the password securely?
If you're using Ansible, it's easy.
Let's jump in.