Using Ansible Vault with Environment Variables
Nov 15, 2025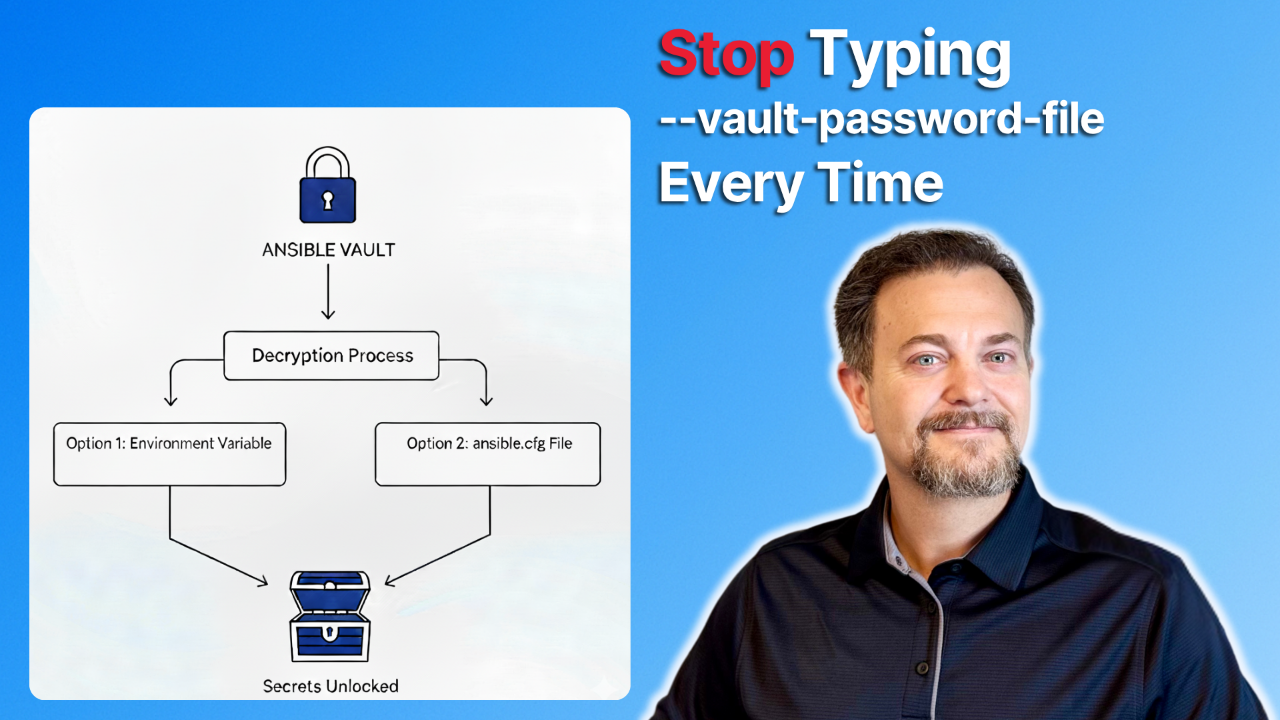
We've reached the final post in our Ansible Vault series. We've come a long way and have just scratched the surface on how Ansible Vault can be used to help secure automation.
You've learned to stop hardcoding passwords by encrypting entire files. You've mastered surgical security by encrypting single variables. And in our last post, you unlocked true, unattended automation by using a vault password file.
But there's one last piece of "friction" in our day-to-day workflow.
Typing --vault-password-file ~/.ansible/vault_pass.txt every single time you run a command is repetitive. It's a minor annoyance, but it still creates friction. What if you forget? What if you're switching between projects and type the wrong path?
Let's learn how to make Ansible automatically find our password file using environment variables. We'll use the example playbooks and variables used previously.
Environment Variables
Before we jump into the examples, environment variables might be a new concept. By setting an environment variable, you are telling your terminal session, "Hey, if Ansible ever needs a vault password, this is the file it should use by default."
The change is subtle, but your command line becomes short again:
ansible-playbook test-inline-vault.yml
Ansible knows how to use the file you set in your ANSIBLE_VAULT_PASSWORD_FILE environment variable. There are many environment variables that Ansible can use (this topic could be a whole series on its own). Check out the complete list here if you're interested.
There are two primary ways to set this variable.
Method 1: The Session-Based Environment Variable
You can set the ANSIBLE_VAULT_PASSWORD_FILE environment variable for your current terminal session. Ansible is programmed to automatically look for this variable.
Since the ansible-playbook command runs inside a Linux environment, you'll use the export command.
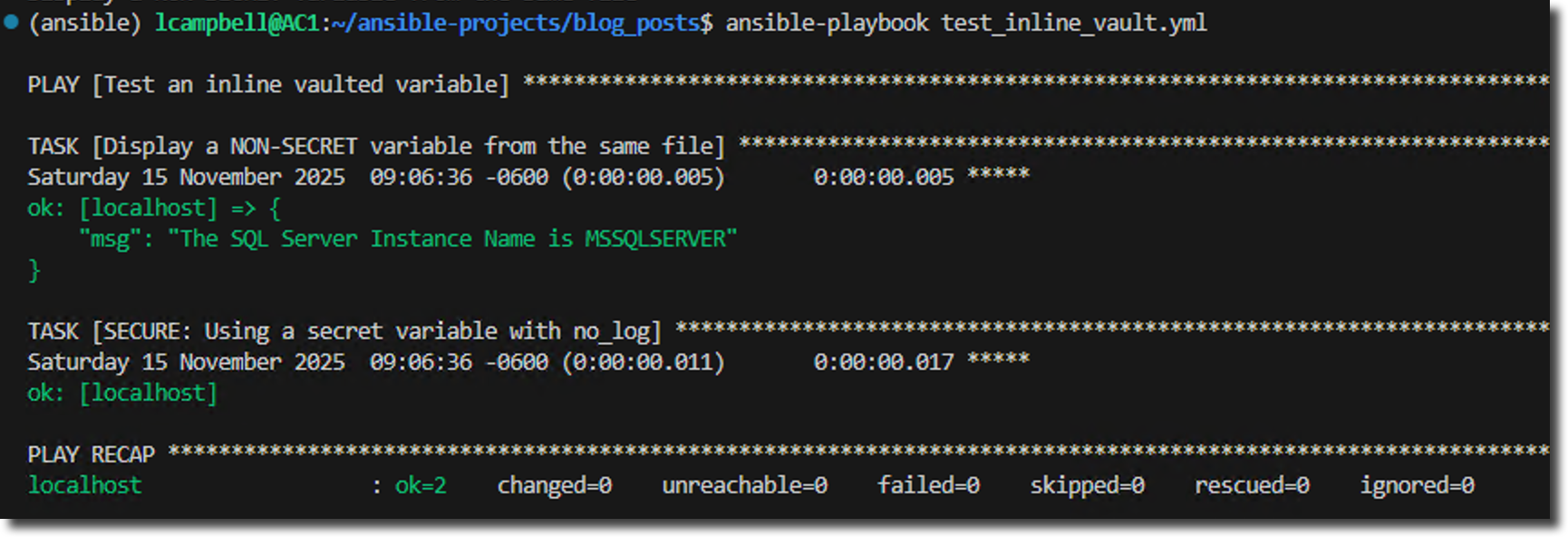
export ANSIBLE_VAULT_PASSWORD_FILE=~/.ansible/vault_pass.txtIt runs without prompting for the password file. Ansible finds the environment variable, reads the password from the file, and decrypts your secrets in the sqlservers.yml group var file.
Method 2: The ansible.cfg File
Ansible looks for a file named ansible.cfg in your project's root directory. You can define the vault password file path inside this configuration file.
1. In the same directory as your playbooks, create a new file named ansible.cfg.
2. Add the following content. This tells Ansible to look for a vault password file named vault_pass.txt in the ~/.ansible directory (remember, keep the password file separate from your project folder).
[defaults]
vault_password_file = ~/.ansible/vault_pass.txt
3. Save the file. You can safely commit ansible.cfg to source control.
4. Now, unset the variable you set in method 1 by running - unset ANSIBLE_VAULT_PASSWORD_FILE.
5. Run your playbook with no vault arguments - ansible-playbook test_inline_vault.yml.
It works without having to set an environment variable in each session. Anyone who clones your project and creates their own vault_pass.txt file (as instructed in your README) in their home .ansible directory will have a workflow that works on their machine.
Conclusion
Over the past 5 weeks, we've covered why storing plain-text passwords in your scripts is a security risk that can have serious professional consequences.
- Introduction to Ansible Vault.
- Securely store groups of secrets in an encrypted file.
- Surgically protect individual secrets within plain-text files.
- Automate playbooks to run unattended with a password file.
- Streamline your entire workflow with ansible.cfg.
Get free access to my "SQL Server Automation: Your First Steps with Ansible" Guide
Get started with Ansible using this free guide. You'll discover how simple Ansible is to use, understand core concepts, and create two simple playbook examples.
When you signup, we'll send you periodic emails with additional free content.
