We've reached the final post in our Ansible Vault series. We've come a long way and have just scratched the surface on how Ansible Vault can be used to help secure automation.
You've learned to stop hardcoding passwords by encrypting entire files. You've mastered surgical security by encrypting s...
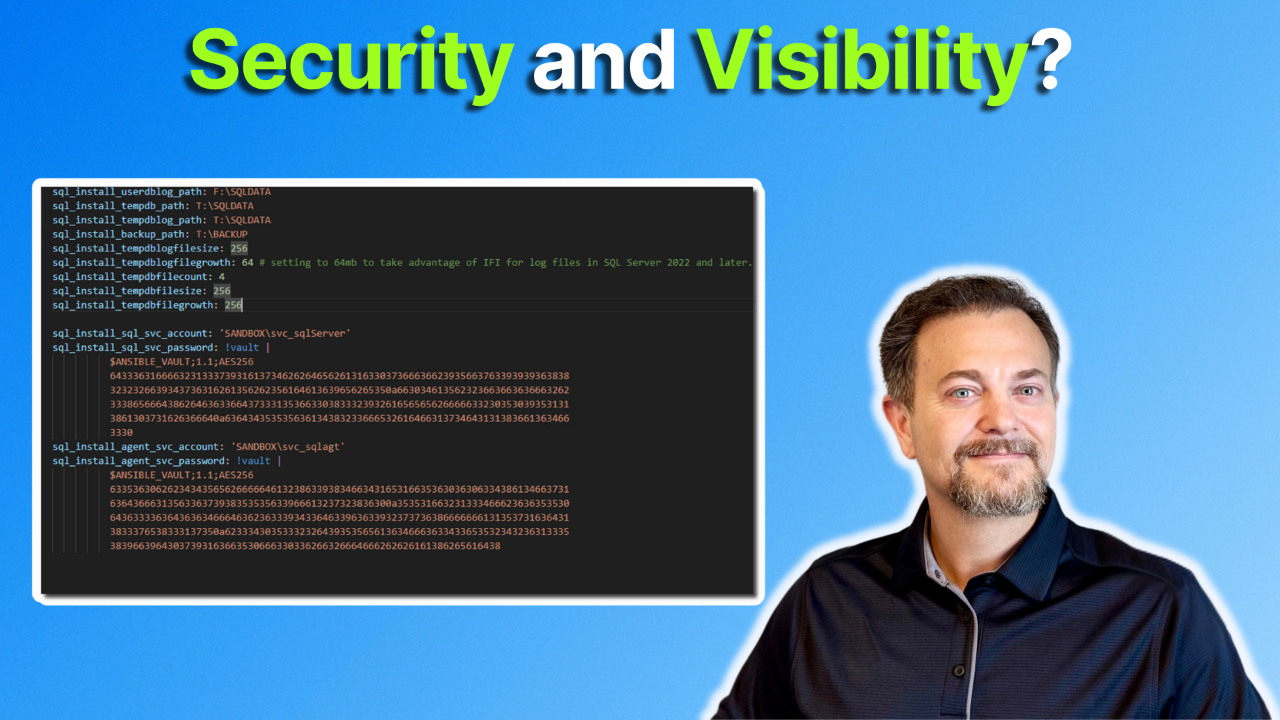
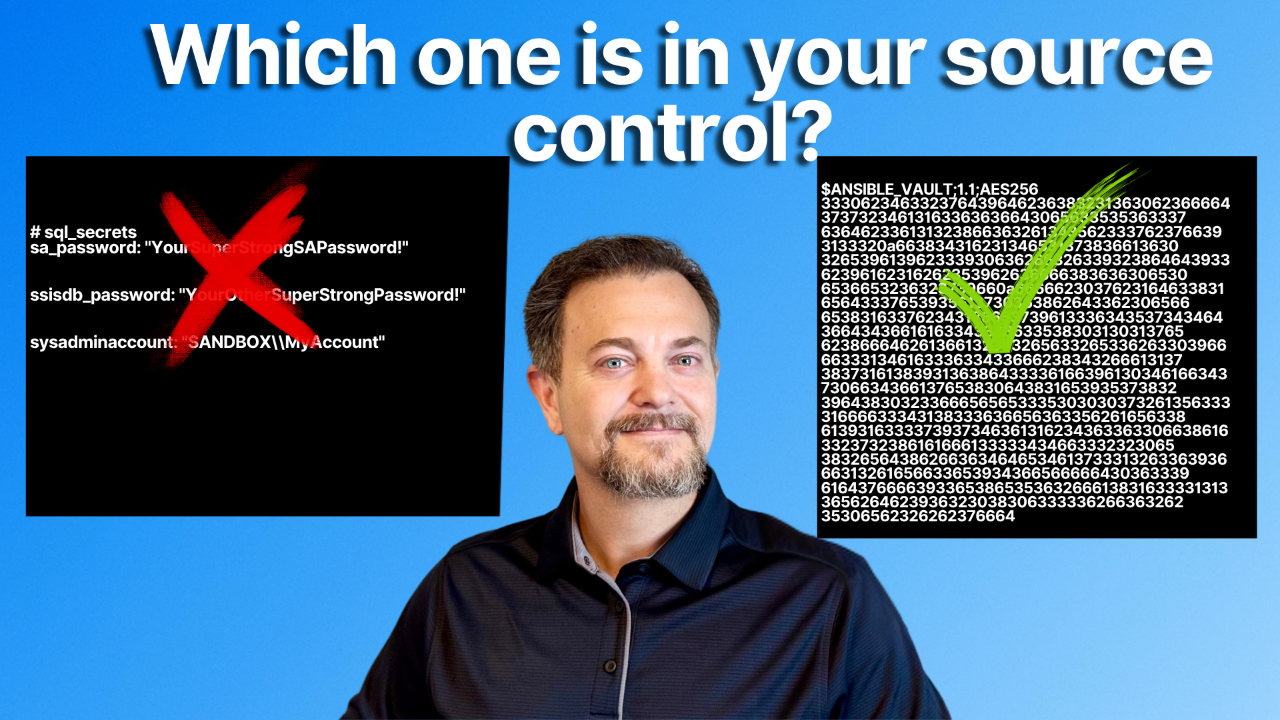
Over the past few weeks, we've explored Ansible Vault, learning about its purpose and how it can be utilized. You can create fully encrypted files and perform granular, inline encryption on single variables. Your secrets, hopefully, are no longer stored in plain text.
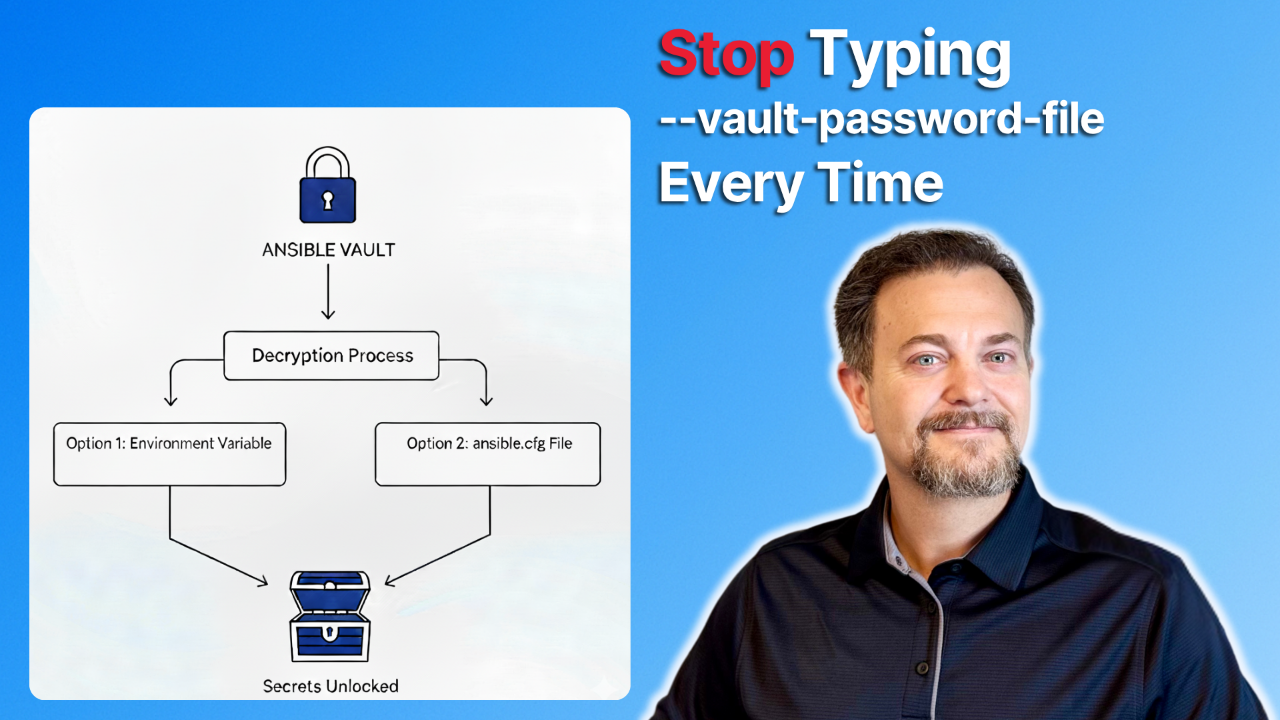
But there's still one manual...
In our last post, you learned how to create a fully encrypted file with ansible-vault create. This is the perfect solution for grouping a set of related secrets, like all the credentials for a new SQL Server build.
But what happens when you don't need to lock down an entire file?
Sometimes, you h...
Last week, we discussed the ticking time bomb of hardcoded passwords and why secure secrets management is a non-negotiable skill for DBAs. We identified Ansible Vault as the right tool for the job, but theory only gets you so far.
Today, we get our hands dirty.
We're going to take our first step ...
How many times have you applied a configuration change and SQL Server restarted, even though nothing actually changed?
- Scripts run blindly
- Unnecessary downtime interrupts users
- You lose trust from the business because "maintenance" caused avoidable outages.
Fragile scripts don't know the dif...
In our last post, you learned how to stop writing brittle scripts by using Ansible Facts. Your automation is now intelligent–it can discover a server's environment and adapt its actions accordingly. It's a big step forward.
But with that success comes a new, more complex challenge: scale.
You're...
Last week, we unlocked the "Golden Rule" of safe automation: idempotency. You now know that a reliable playbook leaves your system in the desired state, regardless of how many times you run it. That confidence allows you to do more than just report; it lets you change things safely.
But what if y...
Last week, you took a massive step.
You built your first Ansible playbook, ran it, and saw for yourself that a different way of managing SQL Server is not only possible but within your reach. You had your first win as an Automation Architect.
But with that first success comes a new, perfectly va
...Last week, we talked about the two paths a DBA's career can take: the reactive, problem-fixing "Mechanic" and the proactive, system-designing "Architect." You're here because you know the future is in building systems, not just fixing them.
But the journey from Mechanic to Architect can feel daunt...
Over the past several blog posts, I've been talking about patching. More specifically, patching SQL Server Availability Groups using the rolling update method. We defined the inventory file, tasks, and built supporting PowerShell scripts along the way. But, I'd like to back up a bit. Why would y...
The following information is based upon SQL Server 2025 CTP 2.1 and is subject to change upon release.
Recently, I've been updating the Ansible playbooks and the mssql Ansible role to support SQL Server 2025. This role and playbook are used throughout the Ansible for SQL Server DBAs course, and I ...
If you're automating your SQL Server 2025 installations on Windows with Ansible over SSH (passwordless login), you might hit a cryptic error that stops you in your tracks. I recently ran into this, and the solution is all about understanding Kerberos delegation.